Since the core focus of my firm is on information security, and nothing seems to inspire an entrepreneurship-related post, today's Chautauqua shall be on firewalls and bloated rulesets.
In most small-medium enterprises, the maximum number of firewalls I've seen is about 4-5, usually always less than a dozen. But as the size of the organization grows, not only does the number of firewalls increase, but the complexity of the ruleset within the firewall also increases. Sometimes exponentially. This is aided by weak change management processes, where users simply request the change, their department manager approves it, and the security team implements it. As time progresses, the ruleset becomes bloated and reduces the performance of the firewall, since the firewall needs to process the rules in sequence for each packet that arrives until a match is found.
One of our clients has more than a 100 firewalls from three different vendors, and the ruleset varies from a manageable 500 rules to an insane 80,000 rules in one of the Cisco PIX firewalls! There are various reasons that have contributed to this situation:
- The weak change management process referred to earlier
- Security administrators not checking if a rule to process the same type of traffic has already been added
- They do not check if the new request can simply be grouped with an earlier request
- If the request is of a temporary nature, they do not check periodically to remove temporary rules.
- Analyze the logs to determine which rules were actually being used by the traffic flowing through the firewall
- Analyze the configuration to determine redundant rules or groupable rules
- Analyze the rule creation process and inhibit rule creation at that stage as well
- Takes as input the filename containing the firewall configuration, and reads this into a database table.
- Analyzes the firewall logs over a given period of time to determine rules, which are being used, and marks the others for deletion
- Analyzes rules, which are redundant. I.e., there is some other rule of which this rule is a subset. Thus this rule can be dropped.
- Analyzes rules, which can be grouped. If the source and the destination IP addresses are the same, then the ports/services for two rules can be grouped together to create one single rule
- Analyze the other components of the configuration, which are not being used and remove those as well.
Initial runs of the tool are resulting in a reduction ranging from 40-60% of the ruleset. Here's a snapshot of the rudimentary GUI we've built. It shows the output for a Cisco PIX firewall, which has been analyzed and a new configuration can be created with the commands listed:
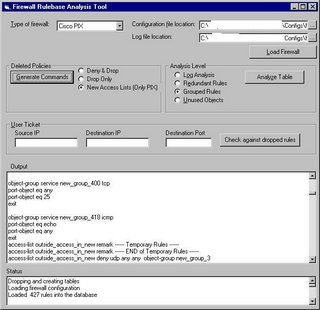
For the first two firewalls it produces the output in the actual configuration commands to change the configuration. You could simply copy-paste the output onto the command-line interface (CLI) of the firewall. For Cyberguard, it simply shows the rules and the rule numbers, and these need to be manually dropped from the GUI configuration.
Some further references on the same subject:
Firewall Policy Advisor for anomaly discovery
Taxonomy of conflicts in firewall policies
An expert system for analyzing firewall policies
Other products that might be doing the same thing are Algosec and Firemon.
Incidentally, this project has enabled me to gain a much deeper insight into the various firewalls. And I must say Netscreen firewalls are amazingly good, and Cisco PIX has way too many shortcomings. The Cyberguards fall somewhere in between. Checkpoint hasn't been included in the list, but we might include that in the tool's capabilities as well.



3 comments:
What do you think about ZoneAlarm Pro firewall?
Well, the current post was on enterprise firewalls, and ZoneAlarm is a personal firewall - a very good one too! I'd suggest you give BlackIce a shot as well. It's got pretty cool IDS capabilities besides the firewalling. Also, check out Microsoft's OneCare security service.
A very interesting article - where can I find more information about the tool?
Thanks
Post a Comment